5 Mobile Botnet Threats
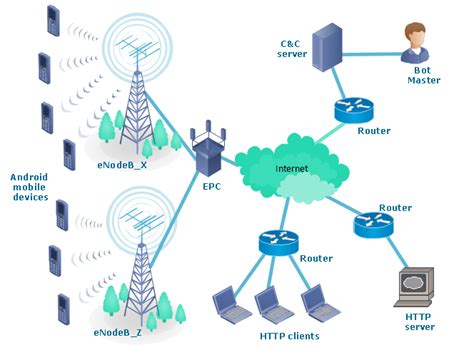
The rise of mobile devices has led to an increase in mobile botnet threats, posing significant risks to individuals, businesses, and organizations. Mobile botnets are networks of compromised mobile devices that are controlled remotely by attackers to carry out malicious activities. These threats can compromise sensitive information, disrupt services, and cause financial losses. In this article, we will explore five mobile botnet threats that you should be aware of.
Key Points
- Mobile botnets can compromise sensitive information and disrupt services
- Malware-based botnets are a significant threat to mobile devices
- DDoS attacks can be launched from mobile botnets
- Mobile botnets can be used for spamming and phishing
- Cryptojacking is a growing concern for mobile devices
Malware-Based Botnets

Malware-based botnets are one of the most significant threats to mobile devices. These botnets are created by infecting mobile devices with malware, which can be spread through various means such as malicious apps, phishing emails, or infected websites. Once a device is infected, it can be controlled remotely by the attacker to carry out malicious activities such as stealing sensitive information, sending spam messages, or launching DDoS attacks. According to a report by Kaspersky, malware-based botnets account for over 70% of all mobile botnet threats.
Types of Malware-Based Botnets
There are several types of malware-based botnets that target mobile devices, including Trojans, Ransomware, and Adware. Trojans are malicious programs that disguise themselves as legitimate apps, while ransomware encrypts data and demands payment in exchange for the decryption key. Adware, on the other hand, displays unwanted ads on the device. Each of these types of malware can be used to create a botnet, making them a significant threat to mobile devices.
| Malware Type | Description |
|---|---|
| Trojan | Disguises itself as a legitimate app |
| Ransomware | Encrypts data and demands payment |
| Adware | Displays unwanted ads on the device |

DDoS Attacks

DDoS (Distributed Denial of Service) attacks are another significant threat posed by mobile botnets. In a DDoS attack, a large number of compromised devices are used to flood a website or network with traffic, causing it to become overwhelmed and unavailable. Mobile botnets can be used to launch DDoS attacks, which can have devastating consequences for businesses and organizations. According to a report by Akamai, DDoS attacks launched from mobile botnets increased by over 50% in the past year.
Consequences of DDoS Attacks
The consequences of DDoS attacks can be severe, including financial losses, reputational damage, and disruption of services. In addition, DDoS attacks can also be used as a smokescreen for other malicious activities, such as data breaches or malware infections. It’s essential for businesses and organizations to have a robust security strategy in place to prevent and mitigate DDoS attacks.
Spamming and Phishing
Mobile botnets can also be used for spamming and phishing, which can compromise sensitive information and disrupt services. Spam messages can be sent to a large number of devices, causing annoyance and disrupting communication. Phishing attacks, on the other hand, can be used to steal sensitive information such as login credentials or financial information. According to a report by Microsoft, spam and phishing attacks account for over 90% of all malicious emails.
Preventing Spamming and Phishing
Preventing spamming and phishing requires a combination of technical and non-technical measures. This includes installing anti-spam software, avoiding suspicious emails, and educating users about the risks of phishing attacks. It’s also essential to have a robust security strategy in place to prevent and mitigate spamming and phishing attacks.
Cryptojacking
Cryptojacking is a growing concern for mobile devices, where attackers use compromised devices to mine cryptocurrency. This can cause significant damage to the device, including reduced performance, increased battery consumption, and heat generation. According to a report by Trend Micro, cryptojacking attacks increased by over 200% in the past year.
Preventing Cryptojacking
Preventing cryptojacking requires a combination of technical and non-technical measures. This includes installing anti-virus software, avoiding suspicious apps, and keeping the device’s operating system up to date. It’s also essential to have a robust security strategy in place to prevent and mitigate cryptojacking attacks.
What is a mobile botnet?
+A mobile botnet is a network of compromised mobile devices that are controlled remotely by attackers to carry out malicious activities.
How can I prevent mobile botnet threats?
+You can prevent mobile botnet threats by installing anti-virus software, avoiding suspicious apps, keeping your device's operating system up to date, and educating yourself about the risks of mobile botnets.
What are the consequences of a DDoS attack?
+The consequences of a DDoS attack can be severe, including financial losses, reputational damage, and disruption of services.
In conclusion, mobile botnet threats are a significant concern for individuals, businesses, and organizations. It’s essential to be aware of the different types of mobile botnet threats, including malware-based botnets, DDoS attacks, spamming and phishing, and cryptojacking. By taking preventive measures and having a robust security strategy in place, you can protect yourself and your organization from these threats.



